Finder's Fee by mango, Tyr, cstef
Description
You gotta make sure the people who find stuff for you are rewarded well!
Escalate your privileges and uncover the flag.txt in the finder user's home directory.
Press the Start button in the top-right to begin this challenge.
First, we need to connect to the machine via SSH with the following command:
# Password is "userpass"
At this point, we are connected as user, and we know the flag.txt file is located in the finder user's home directory (/home/finder/flag.txt). It appears that we can use wget, so let's download linpeas.sh to help identify potential privilege escalation vectors:
However, the machine crashes consistently when running linpeas.sh. To avoid this, we can disable some of the more resource-intensive checks and try again:
Upon running this, we found a privilege escalation opportunity involving the find command, which has the SGID bit set with the user finder.
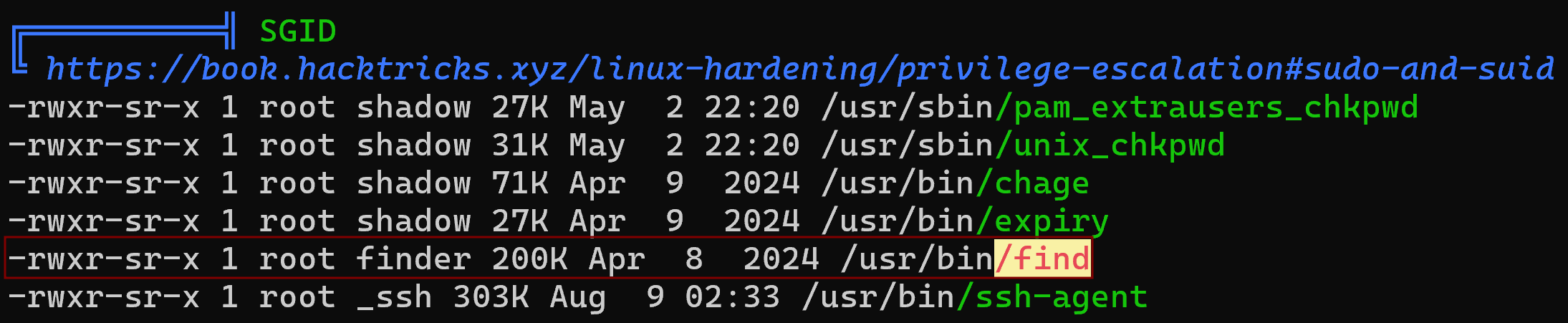
Using this, we can read the flag.txt file with the following command:
The flag is: flag{5da1de289823cfc200adf91d6536d914}